
EMDAD HAQUE
I am a seasoned IT Systems Engineer and Solution Architect specializing in systems design & administration,
virtualisation, networking, code development and automation for on-prem and Azure / AWS cloud infrastructure.
View a list of my projects
View my certifications on Credly
View my career history on LinkedIn
Download my Résumé: pdf -- doc
Automate JIT RDP Access to Azure VMs with Approvals using MS Forms and Azure Logic Apps
Date: 6 Dec 2024
Scenario: In this environment, end users often require RDP access to specific Azure VMs that are publicly available i.e. acting as bastion hosts. Moreover, the access requirement is temporary.
Requirement: For security hardening, only Just-In-Time (JIT) RDP access needs to be provided in order to lock down the access to a specific public IP for a specific duration, and to ensure the request is approved first.
Aim: Currently, the end-user creates a ticket for RDP access to a specific Azure VM and provides their pubic IP that needs to be allow-listed.
This ticket gets assigned to the Azure Admin team, who evaluate the request and create the JIT access to the VM using the Azure Portal or CLI.
As you can imagine, this manual process is slow and dependent on an Azure Admin’s availability.
The goal is to automate this process in a way such that end-users can request the JIT access by providing the required information, and an approver (who can be a non-admin user) can allow it, so that the JIT access is provided without need for an admin user to get involved.
Background:
JIT access to Azure VMs is a feature of MS Defender for Cloud. You can learn more about it from MS Learn - Understanding just-in-time (JIT) VM access.
The process to enable JIT is described in this MS Learn - Enable just-in-time access on VMs.
In short, an Azure admin will set up the Azure VM to be protected by JIT and create rules for the JIT access policy. For example, a rule for allowing inbound traffic on port 3389 will be set up for RDP access.
After that, a user with the correct role/permissions can provide JIT access by using the rule and specifying the parameters like source IP, protocol, request time (duration).
This creates a temporary rule on the Network Security Group (NSG) attached to the specified VM allowing traffic for the requested parameters in the JIT request. Below, I have discussed in details how I have automated the process so that the JIT access rule is enabled when an end-user’s JIT request is received and approved.
A summary of the steps is listed:
- A M365 Form is used to collect the parameters for the JIT access from end-users
- Every Form submission triggers an Azure Logic App
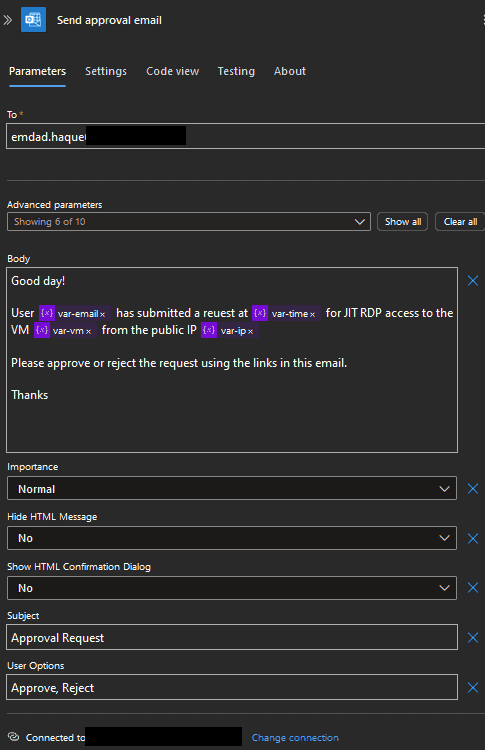
- The Logic App sends an Approval notifications to approvers via email
- Approvers can approve or reject directly from the email itself
- Based on the approval decision and the JIT parameters, the Logic App creates the JIT access
- The Logic app then sends a notification email of the outcome to the end-user/requestor.
Set up MS Forms
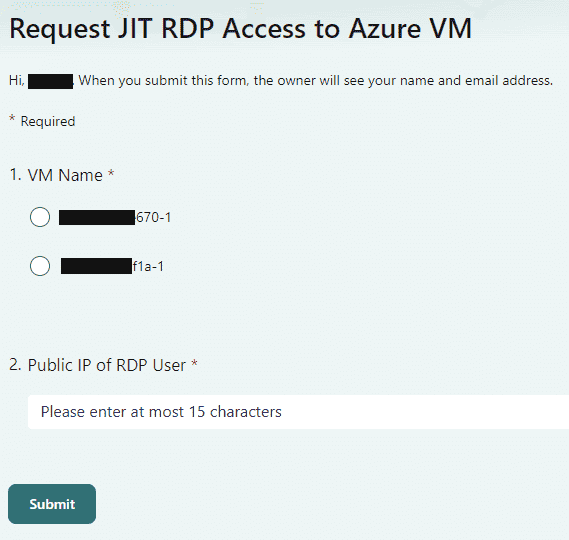
- Create a M365 Form.
For demo purposes, I am using 2 VMs and only asking for the public IP that needs to be allowlisted.
We can ask for other details such as justification, RDP or SSH or some other port, time and duration etc.
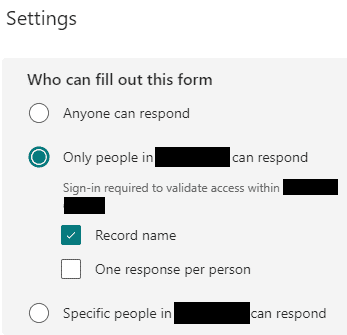
For security, I have allowed only people from my Entra ID tenant to access the form i.e. users will require to sign-in to access the form.
This can be further locked down to a group of users who can access the form.
Set up a Logic App
Create a Logic App and use the Logic App Designer to create the app logic as follows:
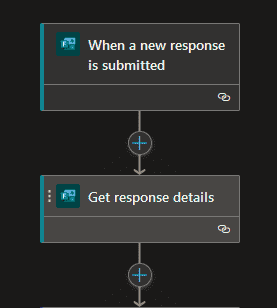
- Trigger the Logic App when a form response is submitted.
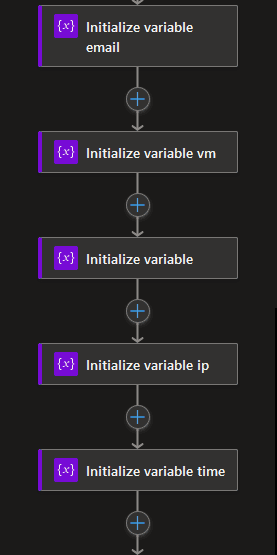
- Initialise the parameters we are collecting from the Form into variables.
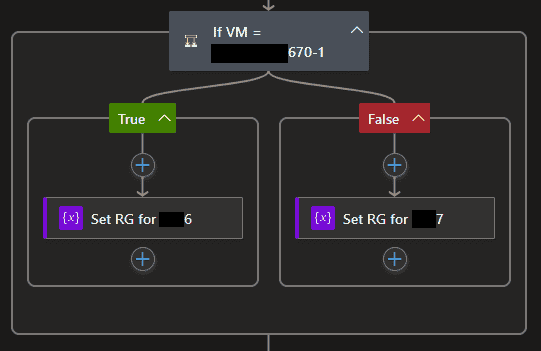
- Depending on the VM name, select the Resource Group. The resource group of the VM needs to mentioned in the HTTP call when requesting JIT access as you can see in the later steps.
- Send an Approval Email to an approver or a group of approvers.
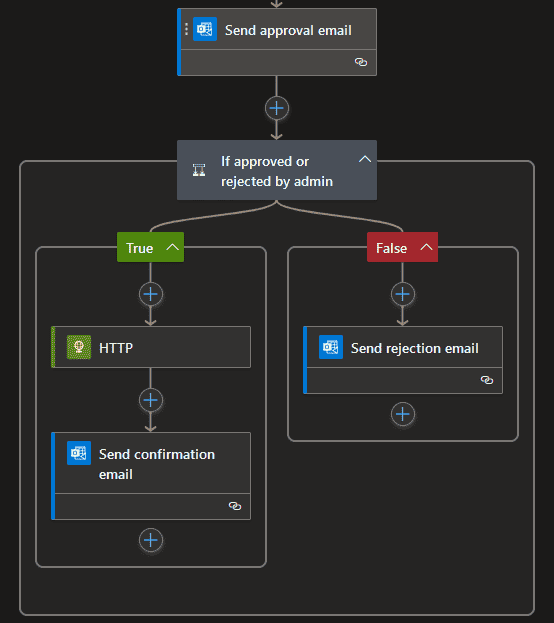
- When Approval is received, use an HTTP request to create the JIT RDP Access and send a confirmation email to the requester.
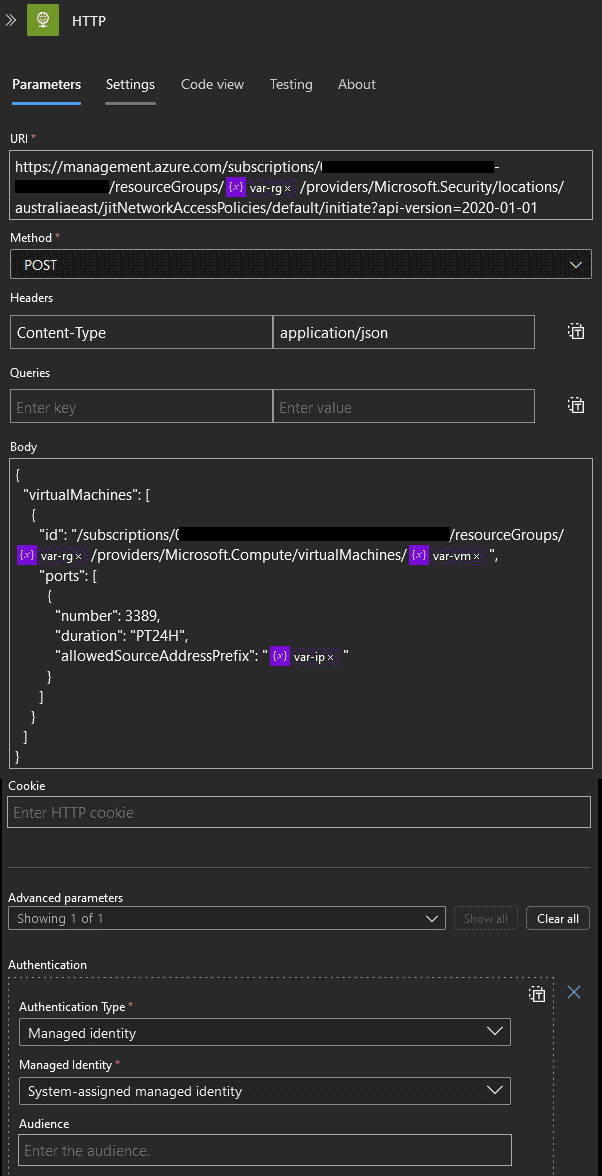
URI:
https://management.azure.com/subscriptions/<sub-id>/resourceGroups/@{variables('var-rg')}/providers/Microsoft.Security/locations/<az-region>/jitNetworkAccessPolicies/default/initiate?api-version=2020-01-01
Method: POST
Body:
{
"virtualMachines": [
{
"id": "/subscriptions/<sub-id>/resourceGroups/@{variables('var-rg')}/providers/Microsoft.Compute/virtualMachines/@{variables('var-vm')}",
"ports": [
{
"number": 3389,
"duration": "PT24H",
"allowedSourceAddressPrefix": "@{variables('var-ip')}"
}
]
}
]
}
- If rejected by approver, send a rejection email to requester.
The confirmation and rejection emails are just simple notification emails without any options unlike the Approval email.
Securing the solution
-
The MS Forms has been secured using settings such that only users who are part of the Entra ID Tenant can access the Form.
This can be further restrcited to a specific group of users in the Entra ID.
-
The Logic App has been assigned a System-Assigned Managed Identity.
A custom role has been created that only allows for requesting JIT access to a VM as described in MS Learn - Enable just-in-time access on VMs - Prerequisites:
- Microsoft.Security/locations/jitNetworkAccessPolicies/initiate/action - Microsoft.Security/locations/jitNetworkAccessPolicies/*/read - Microsoft.Compute/virtualMachines/read - Microsoft.Network/networkInterfaces/*/read - Microsoft.Network/publicIPAddresses/readThe manged identity has been assigned to this role at the Landing Zone Management Group that encompasses all subscriptions with business workload VMs.
This managed identity is used for the HTTP request in the above step.
I hope this was informational and helps you build your own secure solution based on the steps demonstrated here.