
EMDAD HAQUE
I am a seasoned IT Systems Engineer and Solution Architect specializing in systems design & administration,
virtualisation, networking, code development and automation for on-prem and Azure / AWS cloud infrastructure.
View a list of my projects
View my certifications on Credly
View my career history on LinkedIn
Download my Résumé: pdf -- doc
RDP to an Azure VM using MS Entra ID credentials
Date: 30 Oct 2024
Scenario: The environment has Windows VMs in Azure which are not connected to AD and need to be accessed via RDP. This is mainly going to be used by external partners.
Requirement: Security is priority-zero so the Remote Desktop Connection must occur in a secure manner.
Research:
It is possible to RDP to an Azure Windows VM if it has a public IP and allows inbound RDP connections from the internet at the OS level as well as the Network Security Group (NSG). However, opening RDP connections to the internet is not a security best practice. This method can be further locked down by allowing incoming RDP connections from certain IP addresses and using a non-standard RDP port instead of TCP port 3389.
For more security, we will use a Point-to-Site VPN connection for the Remote Desktop Connection. Other secure connections are possible too such as using Express routes or site-to-site VPNs. We will also use Multi-Factor Authentication as an added measure of security.
This solution could be replaced by Azure Virtual Desktops which would be a more robust solution, however there are times in the real world when we need a quick solution with existing resources.
Prerequisites:
- Set up an Azure Point-to-Site VPN because the VMs will not have public IPs. Follow the steps in this link to set up the VPN.
Steps:
-
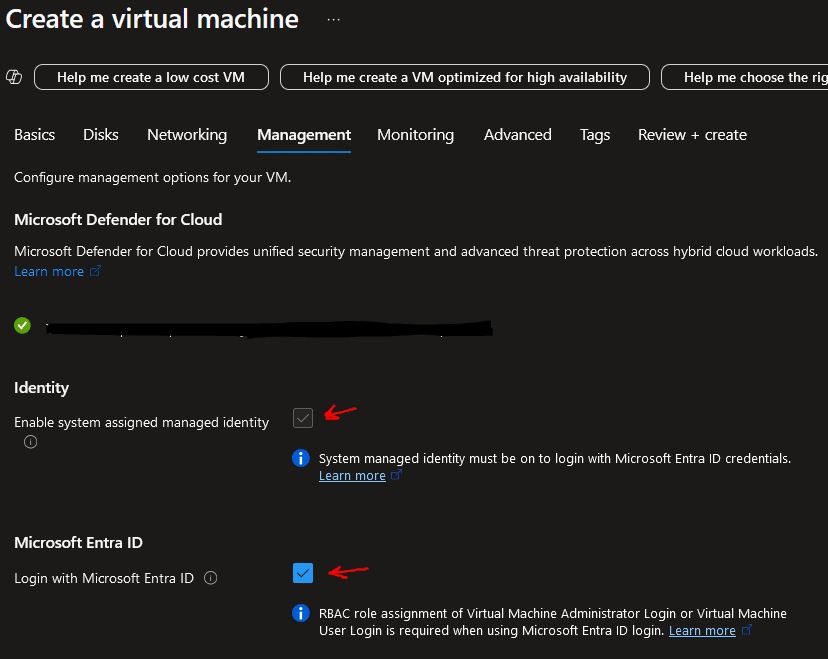
When creating the VM, ensure that you select the “Login with Entra ID” under the Management tab.
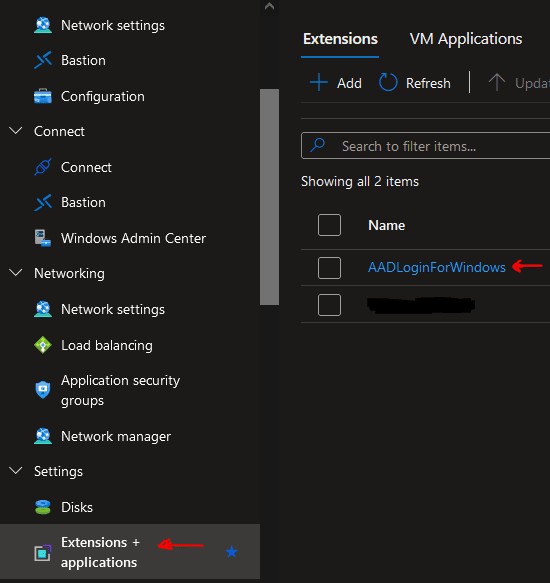
Once the VM is created, under the VM’s “Extensions” you will notice the “AADLoginForWindows” extension, which will allow the RDP access with an Entra ID.
-
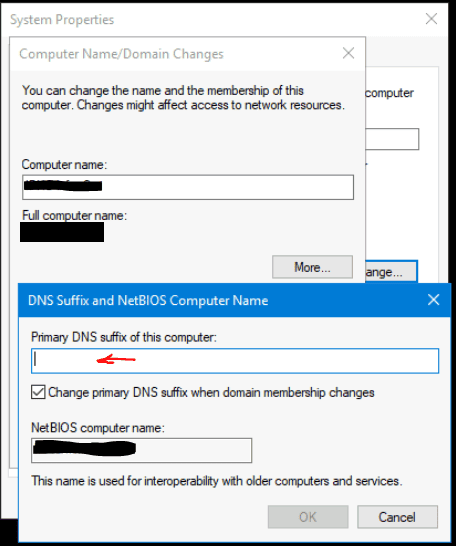
If the VM is not connected to AD, add the DNS Suffix of the network to your VM’s hostname at the OS level.
-
To control who can RDP to the VM as a standard user or as an administrator, use the built-in roles Virtual Machine User Login and Virtual Machine Administrator Login respectively. Go to Azure Portal and select the VM > Access Control (IAM) > Add Role Assignment > Select one of the above roles and the user or group you wish to have this role.
-
To add MFA prompt for the RDP access, create a Conditional Policy that Grants access to Users for All Resources when the MFA Requirement is met. This will cover the RDP access to the VM and require MFA.
-
To RDP to the VM:
-
Connect to the Azure VPN from your local device.
-
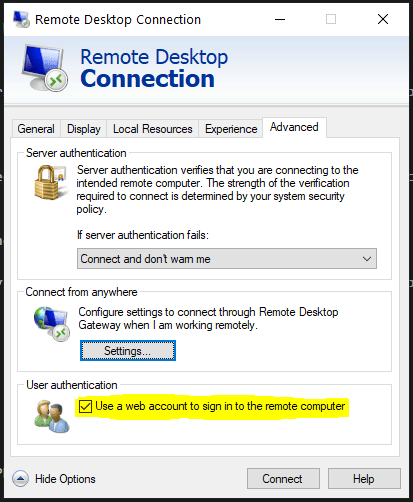
Open Remote Desktop Connection app from your local device and from the Advanced tab, select “Use a web account to sign in to the remote computer”
-
Add the remote computer’s FQDN (OS hostname plus the DNS Suffix)
-
Enter the username, password and MFA code when you the MS Entra ID modern authentication credential prompt.
-
Select Yes when prompted to Allow remote desktop connection?
-
You should now be able to access the Azure VM via RDP using the Entra ID credentials and MFA over a VPN connection. Hope this was helpful.